Push Webhook
Learn how to use the Push Webhook provider to send notifications using Novu
This guide walks you through the entire process of configuring and using Push Webhook with Novu.
The Push Webhook provider is different from other push providers because it does not depend on a third-party service. Instead, Novu sends push notifications directly to a webhook URL that you control. This approach is ideal if you want full control over how notifications are processed, routed, or stored in your system.
Configure Push Webhook with Novu
To configure Push Webhook, you must provide an endpoint URL for Novu to call and a secret HMAC key to verify the request's authenticity.
Step 1: Get your webhook URL and secret key
Before connecting to Novu, you need two things:
- Webhook URL: This is your own API endpoint that will receive the
POSTrequest from Novu. For quick testing, you can use a service like webhook.site. - Secret HMAC Key: This is a self-generated secret string. Novu will use it to encrypt the payload using the
HMAC SHA256algorithm and send the hash in thex-novu-signatureheader. This lets you verify that the request is genuinely from Novu. See how to generate a HMAC key.
POST requests.Step 2: Connect Push Webhook to Novu
Next, add these keys to your Push Webhook integration in the Novu dashboard:
- Log in to the Novu dashboard.
- On the Novu dashboard, navigate to the Integration Store.
- Click Connect Provider.
- In the Push tab, select Push Webhook.
- In the integration form, fill in the following fields:
- Webhook URL: The endpoint URL that you prepared in Step 1.
- Secret HMAC Key: The secret key used to sign webhook calls.
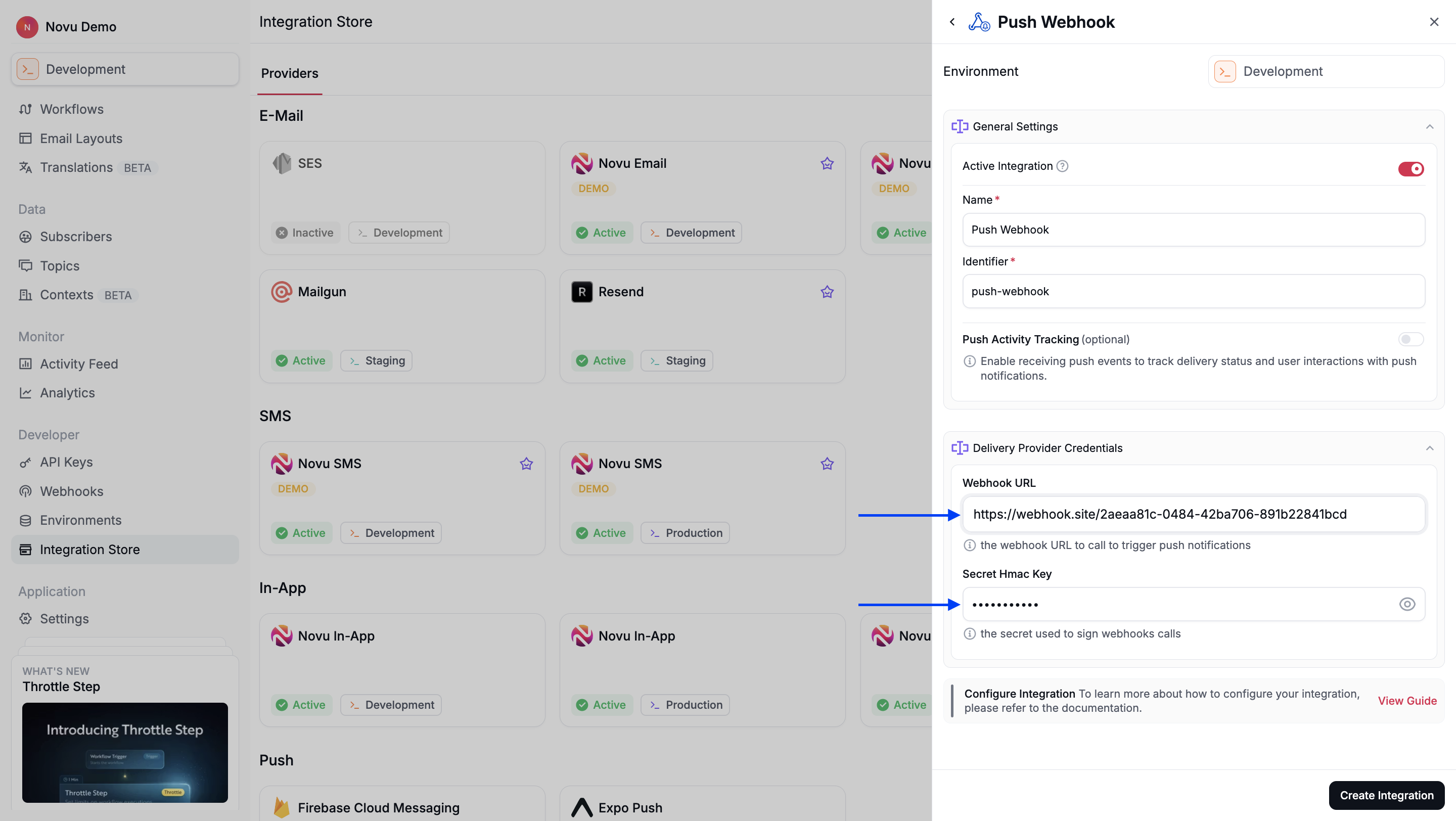
- Click Create Integration.
Using Push Webhook with Novu
Once configured, you must register a device token for your subscriber and trigger a workflow.
Step 1: Add subscriber device token
This step is mandatory. Unlike other push providers that generate a unique token, for the Push Webhook, you must provide your own identifier.
Any random string can be used as a device token. This token is included in the webhook payload sent to your endpoint, allowing you to identify which user or device the notification is for.
Step 2: Send a notification
Now you're ready to send a push notification. Create a workflow with a Push step and trigger it. Novu sends the notification payload to the webhook URL that you configured.
The example below demonstrates a simple trigger using Novu’s SDK.
Payload sent by Novu to webhook URL
When you trigger a workflow, Novu sends a POST request to your webhook URL with a JSON body similar to the one below.
The payload includes:
- The
titleandcontentfrom your workflow editor. - The
target(the device token you set). - Your
overrides. - The full payload from your trigger.
- The subscriber's profile.
Checking authenticity
If you provided a secret HMAC key during configuration, then Novu will include a x-novu-signature header in the request. You can use this header to verify that the request is from Novu and not a malicious third party.
Here is an example of how to validate the hash: